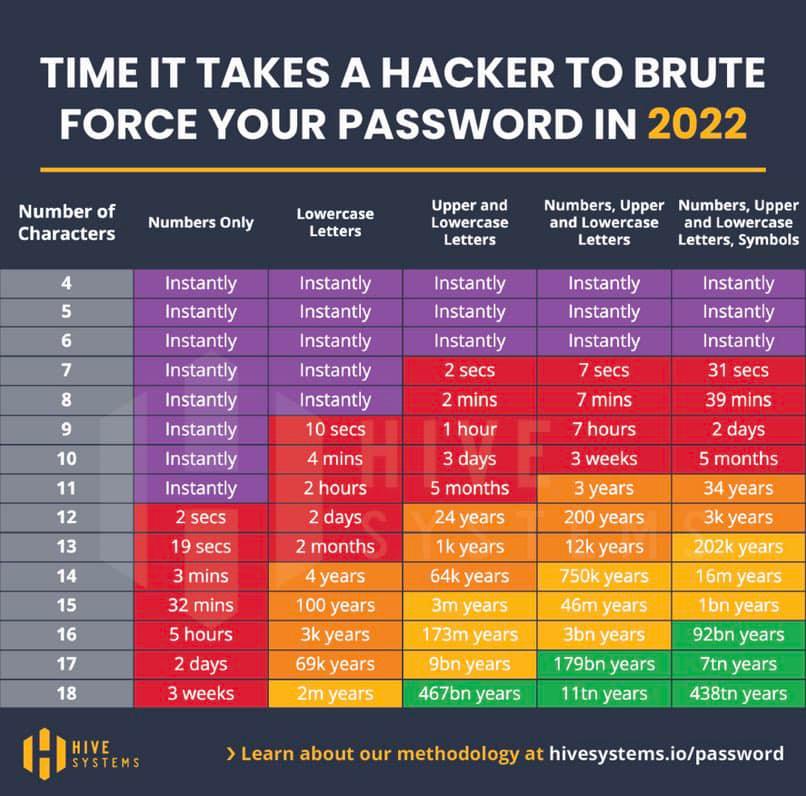
As more companies rely on cloud-based technology, particularly because remote working is so widespread, it’s crucial to ensure systems are secure and confidential data remains protected. Using cloud storage is not necessarily dangerous, but there are some security weaknesses that businesses should be aware of and understand how to prevent.
The following are some of the most common cybersecurity pitfalls:
Data breaches
A key cloud security risk is poor security measures, resulting in data breaches. Businesses must ensure their online storage provider guarantees complete protection against leakage or unauthorised access to personal and sensitive data.
Data loss
Not all cloud service providers are equipped to deal with producing backups when needed, meaning data loss is a risk if businesses do not store their files with an organisation that offers reliable backups.
Data leakage
Cloud services often come with publicly-accessible URLs for uploading and downloading files; this may result in data leakage if improper security controls are used. Businesses must mitigate this risk via strong link encryption and restrictive access.
Account hijacking
Cybercriminals can obtain login information to access sensitive data stored in the cloud and are known to exploit vulnerabilities in network infrastructure, so best practice is to use strong passwords that are changed frequently.
Insider threats
Security threats aren’t only external: administrators, developers and other trusted employees with access to sensitive data may cause damage by accident. Training your staff on how to correctly use cloud software is vital.
Insecure API
Cloud services with insecure APIs threaten the confidentiality and integrity of information and risk the exposure of your data and systems. Typically, there are three types of attacks that hackers will use to try to compromise APIs: brute force attacks, denial-of-service attacks and man-in-the-middle attacks.
No control over repositories
You typically have little control over where your data is stored; if a breach occurs, you may not even be aware if it happened or where. To mitigate this risk, it’s advised that admins understand the security measures at each location and encrypt their data before uploading.
Best practices for risk management

Cloud penetration testing
Cloud penetration testing should be conducted regularly as part of your business’s risk management strategy as it’s an effective and proactive way to assess a cloud-based system’s cyber security strength. It probes vulnerabilities within the cloud, as a real-world hacker would, to test the system.
Contingency planning
Ensure that your online storage provider has a business continuity plan that outlines their strategy for protecting information stored within their servers in the case of any serious emergencies, such as natural disasters or terrorist attacks. You should also ask how often they test this plan to make sure everything works properly.
Data security audit
Ask your service provider whether they perform routine audits of security controls to protect end users’ personal data and sensitive files stored throughout their networks; if not, then you might want to look for another cloud computing partner who can provide complete transparency regarding the security measures implemented by their system’s administrators.
Security training
You should also ask your cloud storage provider if they offer training to help educate staff about potential cyber threats and security risks involved with cloud services. Employees must understand the inner workings of their company’s data management system, especially when it comes to avoiding social engineering attacks on end users’ personal information and files stored remotely.
Customer service
Be aware that many service providers fail to provide 24/7 support for clients, which can be very frustrating whenever problems occur outside office hours. Ask your online storage provider if they offer 24/7 technical support for their customers, or at least ensure you know the average response time to resolve any service-related issues.
Conclusion
There’s no doubt cloud computing provides businesses with access to their important data virtually, from anywhere, without needing to maintain a server. However, with remote access to sensitive and business-critical data, there is a need for sufficient risk management to prevent hackers from breaching cloud applications.
Understanding the risks and vulnerabilities of cloud services is crucial to safeguarding your business against cyber criminals. Cyber security solutions that include cloud penetration testing services will go a long way to providing greater peace of mind for businesses concerned about their cloud security. Cloud pen testing can identify and manage threat monitoring for most cloud service providers and deliver detailed threat assessments to businesses.
Before signing up for a cloud provider, you should check they offer the security your business needs. The more you research, the easier it’ll be to determine which companies offer the best features and security for your needs, as well as which ones have a proven confidentiality track record.
Defense.com believes cyber security should be a priority for everyone and is helping make world-class cyber protection accessible for all companies.